Author: Adam Crompton, Senior Security Consultant
Introduction
The clipboard functionality of modern operating systems has been around for decades, implemented to provide the ability to take a bunch of 1’s and 0’s and store them temporarily. In more common parlance, we know this as the functionality of Copy/Paste, or CTRL-C/CTRL-V. In this relationship, the clipboard is the temporary storage for the items picked up by the copy operation, later to be retrieved by the paste operation.
The intent of this post is not to go on about clipboard functionality, but to make readers aware of the often ignored risk that comes with that functionality.
What is Invoke-ClipboardC2 and Why Was it Created
Over the past fifteen years InGuardians has had the privilege to help many amazing organizations secure their infrastructure. With each new engagement, our clients implement our recommendations and, over time, mature their security posture into a robust and responsive state. In essence, our clients become more secure, more difficult to compromise. This is exactly what we strive for but it also means that for each subsequent penetration test to be successful InGuardians needs to constantly innovate.
On a recent assessment our operators were able to compromise the corporate Active Directory domain, granting us administrative access to the entire corporate network. In this particular assessment, the corporate network was just the first step in compromising more restrictive networks.
With admin access to the corporate domain, our operators were able to determine that users were accessing the restricted network through a variety of methods including jumpboxes, split tunnel VPN, and Microsoft Remote Desktop (RDP). We were also able to gain insight into the tools in use for connectivity to the target network, including password managers and two-factor authentication.
Users accessing the target network were leveraging password safes to store their credentials and using copy/paste to insert the passwords into the login areas. Because they were not ‘typing’ the passwords, traditional keystroke logging was not yielding its usual success. We realized that access to the clipboard would allow us access to a great amount of information missed by a keylogger, such as the copy/paste of credentials and 2FA soft tokens, as well as the possibility to interact directly with the RDP session clipboard. This is how Invoke-Clipboard was born.
What is Invoke-Clipboard?
Invoke-Clipboard is a set of PowerShell tools that weaponizes the Windows clipboard. Invoke-Clipboard has two methods of being called; one for clipboard logging/harvesting (Invoke-Clipboard Logger) and the other for establishing a Command and Control (C2C) channel over the clipboard (Invoke-ClipboardC2C and Invoke-ClipboardC2V).
How Invoke-Clipboard Works
Invoke-Clipboard Logger’s only function is to read from the clipboard and return results for anything that was sent to the clipboard either programmatically or by the user. This can be very useful on a Red Team assessment, as it helps operators profile the target’s daily activities, steal credentials from password safes and any other data sent to the clipboard. In conjunction with a keylogger and timestamped screenshots, attackers can now build a catalog of credentials and associated applications.
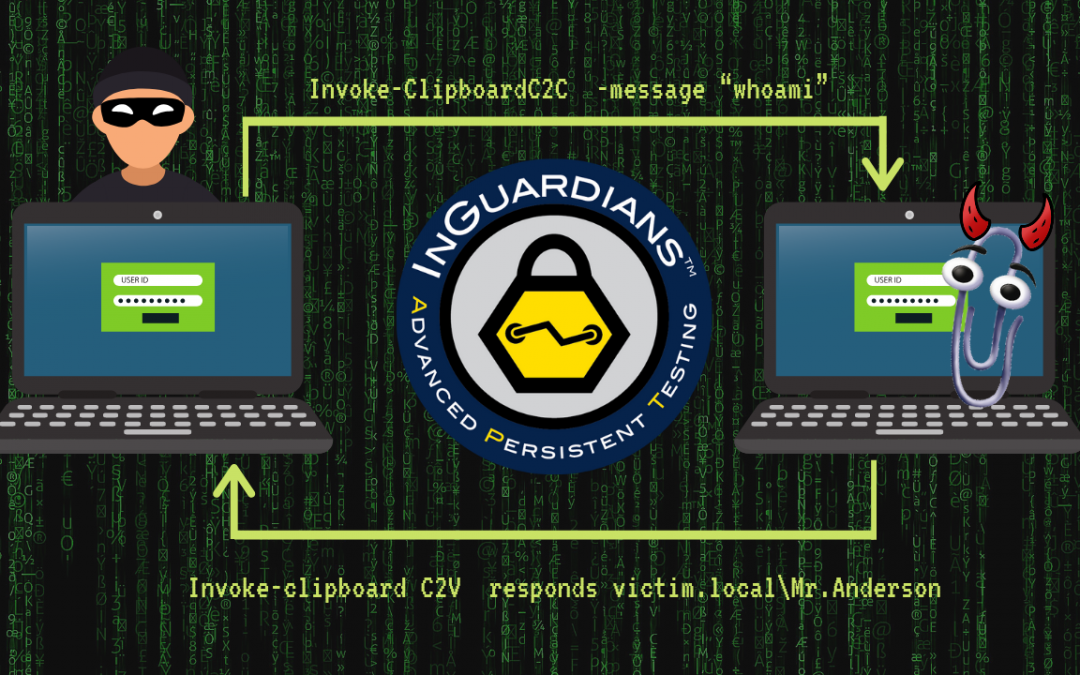
Invoke-ClipboardC2V is the clipboard parsing portion of the C2 running on the victim. This is the script that is deployed on the victim to capture new commands sent by Invoke-ClipboardC2C, execute them on the victim system and return the output to the clipboard for retrieval by Invoke-ClipboardC2C.
Invoke-ClipboardC2C is the client portion of the Command and Control (C2) infrastructure. After a command, the client will sleep until clipboard buffer has changed. Once the clipboard buffer has changed, the results are parsed and sent to the C2 operator.
Demo
The Code
We are finalizing the code for release in conjunction with an upcoming conference talk. We will continue to add additional features in upcoming releases. Meanwhile, we wanted to expose this attack vector in order to challenge the way we think as both attackers and defenders.
Invoke-Clipboard project page: https://github.com/inguardians/Invoke-Clipboard
Conclusions
Who types passwords anymore? Infosec has tasked our users with using unique and complex passphrases for each application. Using password safes and two-factor authentication is considered the current best practice. Copy and paste is the way our users retrieve their creds from these applications. However we see that with tools like Invoke-Clipboard, sensitive data can be harvested by an attacker.
There is one other take away from this scenario; one should never underestimate the extent malicious attackers will go to in order to build a new, previously unknown C2 communications channel
The decision to leave clipboard functionality enabled becomes even more important for critical areas, such as jump boxes and even elevated privilege workstations. With Invoke-Clipboard, the use of clipboard in these areas has increased risk due to exposure and the ability for it to be used for C2 communications.
Adam Crompton has an awesome webinar coming up on February 21 at 12PM PST / 3PM EST with even more detailed analysis of how Invoke Clipboard works!
Webinar recording: https://www.youtube.com/watch?v=qY9thXWItY8
References
- StringToHGlobalUni – https://msdn.microsoft.com/en-us/library/system.runtime.interopservices.marshal.stringtohglobaluni(v=vs.110).aspx
- ClipboardFormats – https://msdn.microsoft.com/en-us/library/windows/desktop/ms649013(v=vs.85).aspx#_win32_Standard_Clipboard_Formats