Feb 18, 2017 | Blog
Original Post Author: Tom Liston [Twitter: @tliston] Original Date Published: 11 June 2013 Doing a Google search for “arduino GPS clock” turns up more than a few other projects that use the time information found within the NMEA data provided by a GPS...
Jan 18, 2017 | Blog
Original Post Author: Don C. Weber [Twitter: @cutaway] Original Date Published: 03 June 2013 Black Hat USA 2013 will include a presentation by Tom Ritter and Doug DePerry titled: “I Can Hear You Now: Traffic Interception and Remote Mobile Phone Cloning with a...
Dec 1, 2016 | Blog
Original Post Author: Don C. Weber [Twitter: @cutaway] Original Date Published: 25 April 2013 Mike Poor (@Mike_Poor) noticed Stephen Northcutt’s blog post about phone spear-phishing. This reminded him of an email that I sent to the Senior Security Analysts here...
Nov 5, 2016 | Blog
Original Post Author: Don C. Weber [Twitter: @cutaway] Original Date Published: 08 April 2013 Accessing memory from embedded devices can be accomplished multiple ways. The easiest methods include using debugging ports or tapping the exposed pins of a Thin...
Oct 22, 2016 | Blog
Original Post Author: Don C. Weber [Twitter: @cutaway] Original Date Published: 28 March 2013 John Sawyer pointed me to a blog post Getting the most out of your pentesting by Wendy Nather of 451 Security. I would like to provide a little bit more context in the hopes...
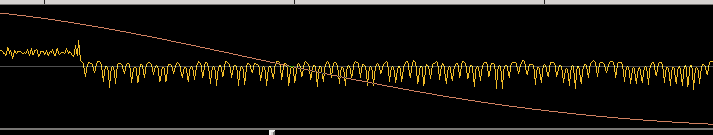
Feb 7, 2016 | Blog
Post Author: Don C. Weber [Twitter: @cutaway] Date Published: 15 May 2014 I have not picked up my HackRF Jawbreaker in a while (Figure 0x0). Family and billable work trump side projects. Lucky for me Tom Liston and I started teaching the Assessing and Exploiting...

